Enumeration – nmap


Web page

Using Gobuster to Find Hidden Web Content


The IP address has changed from 10.10.76.131 to 10.10.181.140.
Interesting folder is /robots. Robots is where the addresses to be are saved
not indexed by search engines. Because the computer does
not to find them, we get such interesting places. Fsociety.dic files
and key-1-of-3.txt are available to anyone on the same network
what machine under test.
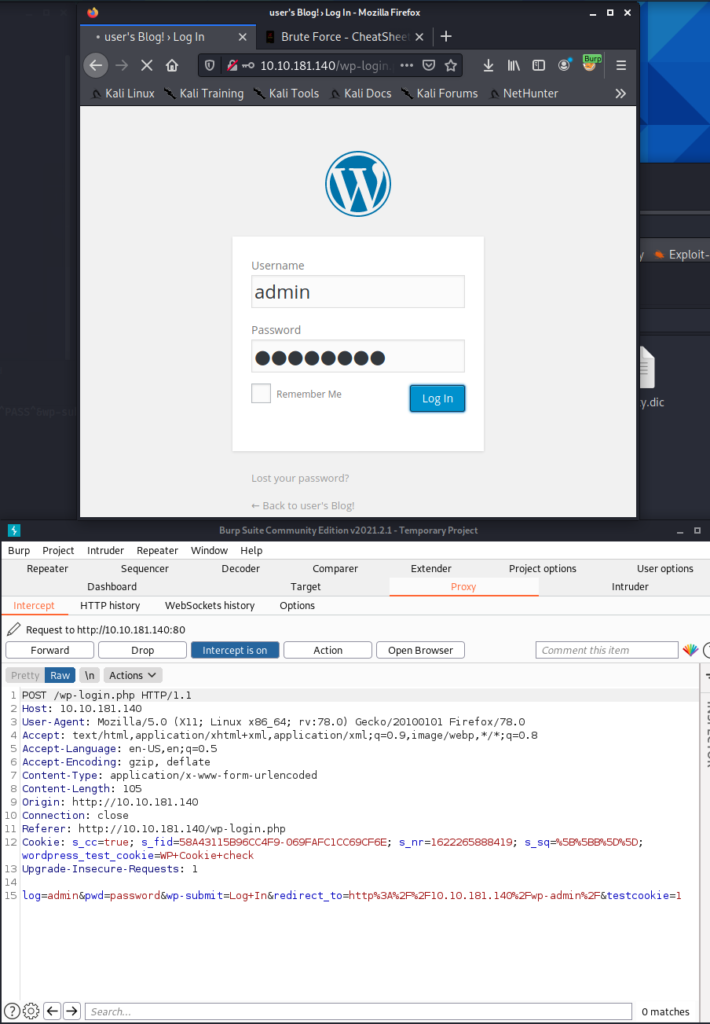
Brute forcing wp-login page





As the attack was prolonged, the fsocit.dic file was checked for
double records. It turned out that the file contains repeated repetitions
records. The sort and uniq command has sorted and deleted duplicate records.
Wordlist length decreased from 858,160 to 11,451 lines.


Brute force has been finished successfully.



At this point, we can see the various files that the page has. In the screenshot
the content of php-reverse-shell (https://github.com/pentestmonkey/php reverse-shell / blob / master / php-reverse-shell.php) was pasted into the CSS file, what is known
is that it won’t work. In the screenshot you can see a column on the right
templates. The file archives.php into which it was pasted is selected
reverse-shell.




The first command executed is python -c ‘import pty; pty.spawn (“/ bin / bash”) ’
which provides the interactive terminal you need for
I go to the / home / root folder where there are two files. Key-2-of 3.txt which I do not have access to like the user deamon and the password.raw file md5 which contains the md5 hash.

Using the hashcat tool, a given hash was cracked within 3
seconds. Obtained password: abcdefghi ..

was in / home / robot then the username must also be robot, a
the password is the previously cracked hash.

Now there is the last stage, which is the escalation of privileges. The easiest way
escalation on unix systems is finding binaries with special SUID / GUID permissions. To find such files you must execute
find -perm -4000. The rest of the command that is 2> / dev / null is used
to ignore files we do not have access to.

Then the results of this command on our virtual machine and the server to which we gained access were compared. It turned out that the nmap binary is only on hacked server.

The GTFObins page lists all binaries that are useful for this. So I used this knowledge to escalate privileges

That’s all 🙂
